CTEM Stage 4: Validation
Stage Summary: Validation confirms how attacks might work in your environment and how systems (and teams) would react. It turns “theoretically risky” into “practically exploitable” and closes the loop by verifying fixes and defensive controls.
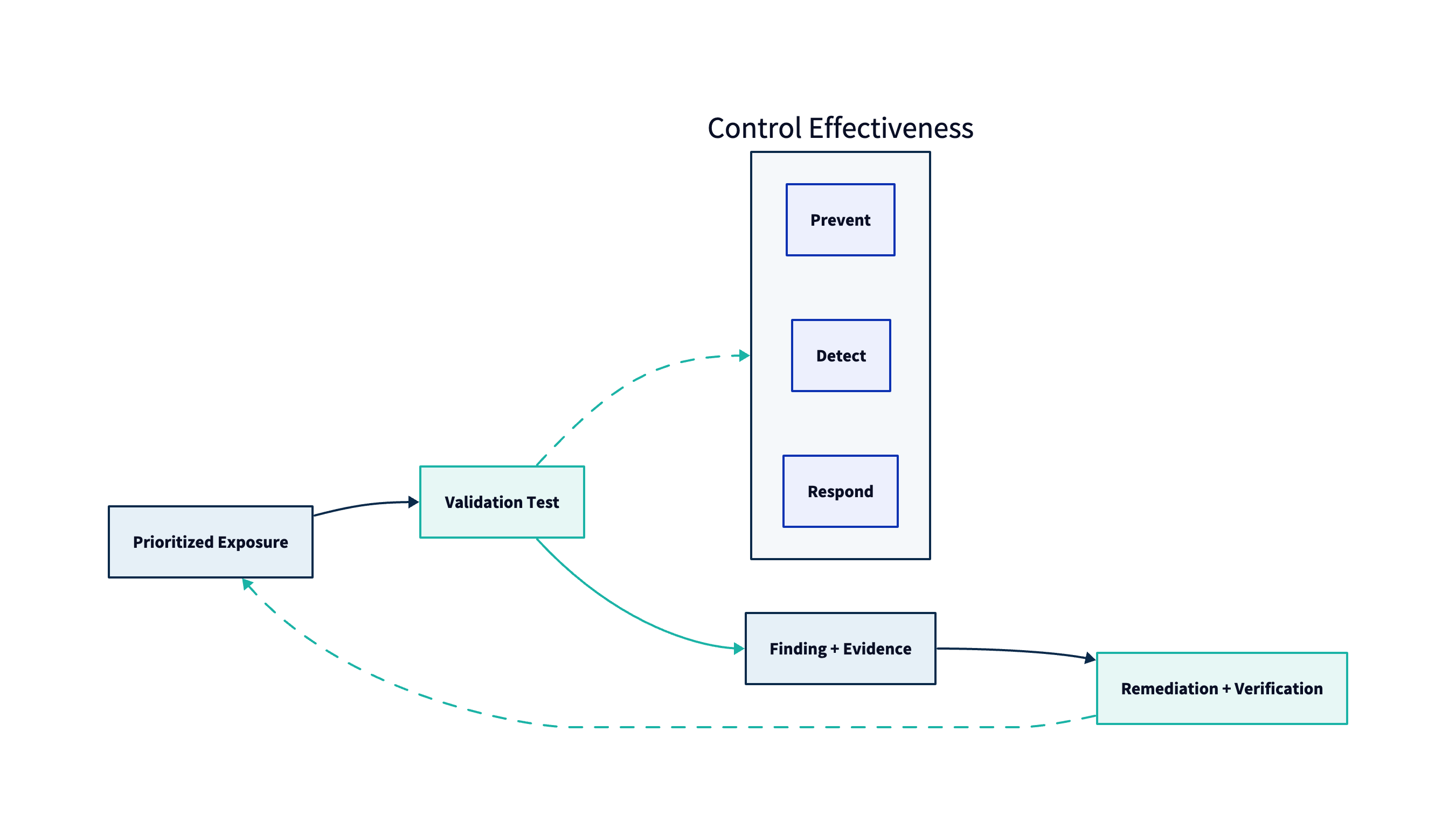
Why Validation Matters
In most enterprises, “we have a vulnerability” is not equivalent to “we are exposed.” Real exploitability depends on prerequisites, reachability, identity posture, and whether compensating controls perform as assumed.
Validation is the mechanism that prevents CTEM from becoming theoretical risk management. It also produces two high-value outcomes beyond exploit confirmation:
- Defensive truth: do controls prevent, detect, and respond the way you believe they do?
- Operational truth: can teams execute remediation safely and verify outcomes?
NIST’s guidance on security testing and assessment emphasizes planning, safety, and repeatability. CTEM borrows that discipline and applies it continuously to the exposures that matter most.
Validation Objectives (Be Explicit)
CTEM validation generally targets one (or more) of the following:
- Exploitability validation
Can an attacker actually exploit the condition (given realistic prerequisites)? - Attack-path validation
Can exposures chain into a path to a high-value asset or business service? - Control validation
Do preventive/detective/response controls behave as expected? - Remediation validation
Did the fix actually remove the exposure (and not introduce new ones)?
Pen tests are valuable, but CTEM validation is continuous, scoped, and directly tied to prioritized exposures and business outcomes.
Key Activities
1. Define Rules of Engagement (ROE) and Safety Constraints
Even “safe” testing can cause outages if you do it carelessly. Your ROE should define:
- Approved environments (prod vs staging vs replicas)
- Non-destructive methods required by default
- Change approvals required for higher-risk tests
- Logging requirements and evidence handling
- Stop conditions (what triggers immediate halt)
ROE template (minimum viable)
| Topic | Policy |
|---|---|
| Test environments | Prefer staging/replicas; production requires explicit approval |
| Data handling | No extraction of sensitive data; redact evidence |
| Operational safeguards | Rate limits, time windows, rollback plans |
| Coordination | SOC informed; on-call coverage confirmed |
| Stop conditions | Any service degradation, unexpected auth behavior, abnormal load |
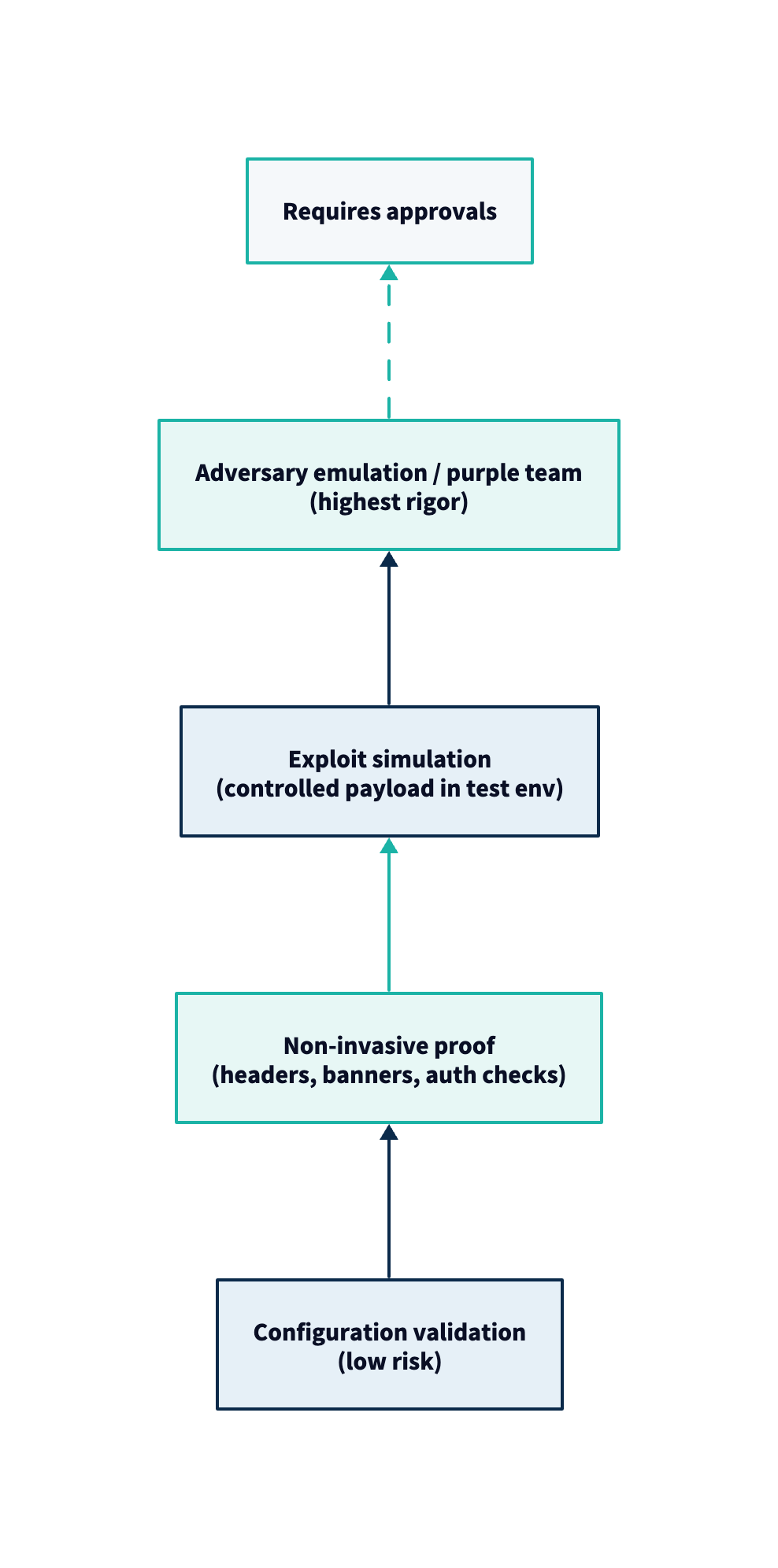
2. Choose Validation Methods Appropriate to the Risk
Validation should be graduated. Start with low-risk verification and escalate only as needed.
Common methods (vendor-neutral):
- Configuration validation: confirm misconfiguration states and policy posture.
- Reachability testing: prove network/access prerequisites (from assumed attacker vantage).
- Controlled exploit proof (safe environments): reproduce exploitability in a lab/staging mirror.
- Adversary emulation / purple teaming: test real-world techniques mapped to your threat model (e.g., ATT&CK-aligned behaviors).
- Control assessments: evaluate security controls against assessment procedures and expected outcomes.
Tie method choice to the exposure type and business service criticality.
3. Map Validation to Threat Behaviors, Not Tool Capabilities
When validation is mapped to adversary behaviors, you get reusable coverage. MITRE ATT&CK is commonly used as a shared language for tactics and techniques.
This enables:
- A repeatable library of test cases (not one-off heroics)
- A defensible control coverage story
- Alignment between AppSec, IAM, Infra, and the SOC
4. Record Findings as Engineering-Grade Evidence
A validation finding should be something an engineering team can act on without debate.
Minimum attributes:
- What was tested (exposure record reference)
- Preconditions required
- Steps performed (high level; avoid sensitive exploit instructions)
- Evidence captured (sanitized)
- Observed control behavior (prevent/detect/respond)
- Business impact mapping (what this enables if abused)
- Recommended remediation options (fix vs mitigate vs accept)
5. Verify Remediation and Prevent Regression
CTEM breaks down when “fixed” means “ticket closed.” Verification should confirm:
- The exposure condition is no longer present
- Control posture remains acceptable
- No equivalent exposure reappears via automation drift
If possible, turn high-value validations into recurring checks (especially for SaaS posture, IAM configuration, and external exposure patterns).
Validation Templates
Template A: Validation Test Case Record
| Field | Example |
|---|---|
| Test case ID | VAL-EXT-001 |
| Exposure type | Internet-exposed admin interface |
| Asset class | Web app / admin plane |
| Threat assumption | External attacker + stolen creds plausible |
| Preconditions | Requires admin login; MFA required (expected) |
| Method | Reachability + auth control validation |
| Evidence | Sanitized screenshots/log references |
| Control behavior | MFA enforced; suspicious login alerted within 5 min |
| Result | Partially effective (alerting works; MFA gaps on service accounts) |
| Remediation | Enforce phishing-resistant MFA for privileged roles |
Template B: Remediation Verification Checklist
- Exposure no longer observable from defined vantage points
- Ownership and status updated in exposure register
- Validation artifacts attached and redacted as needed
- Monitoring rule added (where relevant)
- Regression test scheduled (where relevant)
Common Pitfalls
- Validating in production without guardrails. This is how you create self-inflicted incidents.
- Treating validation as a separate team sport. Validation works best when AppSec, IAM, Infra, and SOC share objectives.
- No linkage to prioritization. If validation findings don’t feed back into the prioritization model, CTEM stops improving.
- Not measuring control behavior. “Exploitable” is only half the story—how quickly can you detect/respond?
- Failure to re-test. Without verification, you accumulate false assurance.
Next Steps
Validated findings should immediately drive execution. Move to Mobilization to operationalize remediation, remove blockers, and report outcomes.
References (non-vendor)
- Gartner CTEM Step 4 emphasis on validation: https://www.gartner.com/en/articles/how-to-manage-cybersecurity-threats-not-episodes
- NIST SP 800-115 (security testing and assessment guidance): https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-115.pdf
- MITRE ATT&CK overview: https://attack.mitre.org/
- MITRE adversary emulation plan resources: https://attack.mitre.org/resources/adversary-emulation-plans/
- NIST SP 800-53A (control assessment approach): https://csrc.nist.gov/pubs/sp/800/53/a/r5/final