CTEM Identifiers
CTEM Identifiers provide a standardized taxonomy for classifying external threat exposures. Each identifier follows a consistent naming convention (CTEM-XXX-#) that categorizes threats by type and provides a unique reference for tracking and management.
Brand Impersonation (BND)
Exposures related to counterfeit products and brand abuse that damage reputation and consumer trust.
| ID | Name | Description |
|---|---|---|
| CTEM-BND-1 | Counterfeit Product Offered for Sale or Use | Counterfeit versions of products being sold on dark web marketplaces, online pharmacies, or e-commerce platforms |
Credential Dump (CRD)
Exposures involving compromised credentials from public breaches or vendor system dumps.
| ID | Name | Description |
|---|---|---|
| CTEM-CRD-1 | Employee Credentials Dumped Publicly | Employee credentials exposed in a public password dump from a third-party breach |
| CTEM-CRD-2 | Vendor System Dump with Credentials | Breached vendor system with credentials offered for sale on dark web forums |
Financial Information Exposure (FIN)
Exposures involving sensitive financial data that could enable fraud or unauthorized transactions.
| ID | Name | Description |
|---|---|---|
| CTEM-FIN-1 | Corporate Bank Account / Routing Information Exposed | Bank account numbers, routing numbers, or payment details publicly disclosed |
| CTEM-FIN-2 | Accounts Payable Information Exposure | Vendor payment details, invoices, or payment schedules publicly disclosed |
Infected Device (INF)
Exposures involving compromised hosts across various ownership categories and risk profiles.
| ID | Name | Description |
|---|---|---|
| CTEM-INF-1 | Infected Corporate-Owned Device | Company-issued device compromised with malware and established persistence |
| CTEM-INF-2 | Infected Vendor-Owned Device | Vendor/contractor device compromised that services the organization |
| CTEM-INF-3 | Infected Employee-Owned Device (Corporate Credentials) | Personal device used to access corporate systems found compromised |
| CTEM-INF-4 | Infected Employee-Owned Device (Personal Use of Corporate Identity) | Personal device using corporate email for personal services found compromised |
| CTEM-INF-5 | Infected Customer-Owned Device | Customer device that interacts with organization services found compromised |
| CTEM-INF-6 | Infected Employee-Owned Device (Internal Network Connected) | Personal device connected to internal corporate network found compromised |
| CTEM-INF-7 | Infected Employee-Owned Device (3rd Party Business Use) | Personal device accessing third-party business services with corporate credentials |
Lookalike Domains (DOM)
Exposures involving deceptive domain registrations that impersonate the organization.
| ID | Name | Description |
|---|---|---|
| CTEM-DOM-1 | Typo-Squatted Domain | Domains with slight misspellings or keyboard proximity errors |
| CTEM-DOM-2 | Homoglyph Attack Domain | Domains using visually similar characters from other alphabets or UTF-8 |
| CTEM-DOM-3 | Phishing Indicator Domain | Domains exhibiting characteristics suggesting phishing intent |
| CTEM-DOM-4 | Brand Impersonation Domain | Domains mimicking official naming conventions to deceive users |
Ransomware (RAN)
Exposures from ransomware attacks affecting the organization's supply chain or customer relationships.
| ID | Name | Description |
|---|---|---|
| CTEM-RAN-1 | Ransom Dump (Supplier) | Supplier/vendor data leaked via ransomware containing organization information |
| CTEM-RAN-2 | Ransom Dump (Customer) | Customer data leaked via ransomware containing organization information |
Source Code Exposure (SRC)
Exposures involving publicly accessible code repositories that may contain sensitive information.
| ID | Name | Description |
|---|---|---|
| CTEM-SRC-1 | Public Repository - Company Sanctioned | Official company repository that may inadvertently expose sensitive information |
| CTEM-SRC-2 | Public Repository - Employee Created | Repository published by an employee without official corporate scrutiny |
| CTEM-SRC-3 | Public Repository - Vendor Owned | Vendor repository containing code related to organization services |
| CTEM-SRC-4 | Public Repository - Unrelated 3rd Party | External repository containing references to the organization |
| CTEM-SRC-5 | Public Repository - Company Comment/Issue | Public comment or issue that discloses information about the organization |
System Exposure (EXP)
Exposures involving internet-accessible systems that could provide attack vectors.
| ID | Name | Description |
|---|---|---|
| CTEM-EXP-1 | Directly Connected Internal System | Internet-accessible system directly connected to internal network (DMZ) |
| CTEM-EXP-2 | Remote Site-Owned System Presumed Connected | Remote site system suspected to have internal network connectivity |
| CTEM-EXP-3 | Corporate Internet-Exposed Gateway Device | Networking device (firewall, router, VPN) exposed to the internet |
| CTEM-EXP-4 | Corporate Cloud-Connected System | System connected to corporate cloud account (AWS, GCP, Azure) |
| CTEM-EXP-5 | Presumed Company System by Branding | System appearing to be company-owned based on branding indicators |
| CTEM-EXP-6 | Contractor/Vendor-Managed System | System managed by third-party contractor or vendor |
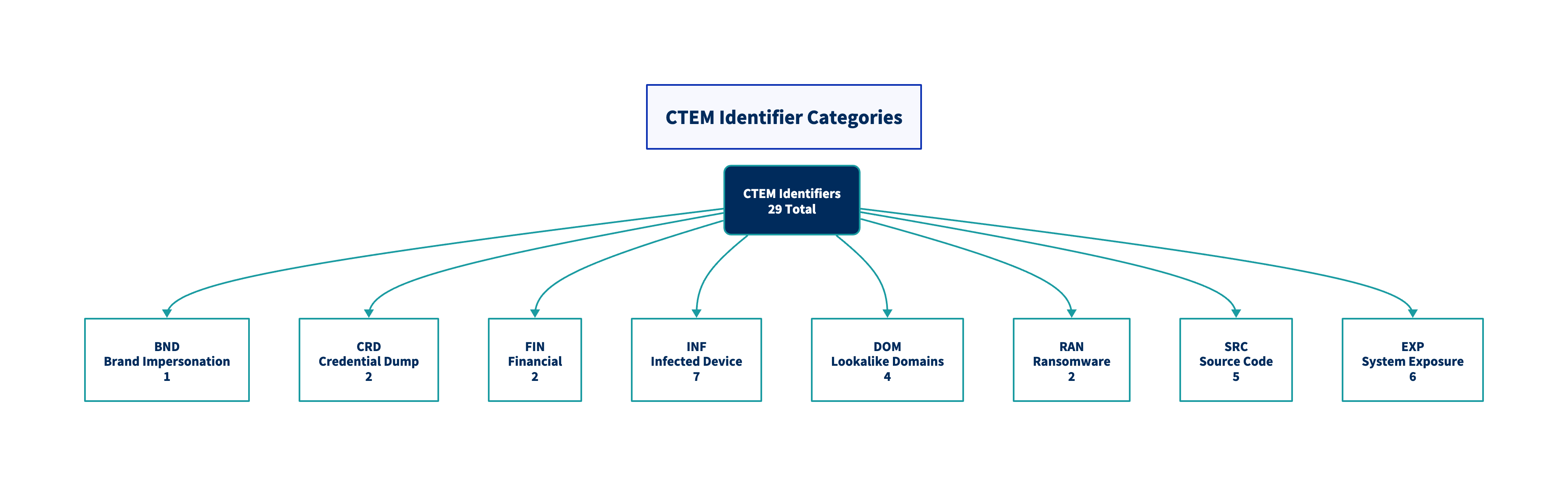
Summary Statistics
| Category | Code | Count |
|---|---|---|
| Brand Impersonation | BND | 1 |
| Credential Dump | CRD | 2 |
| Financial Information | FIN | 2 |
| Infected Device | INF | 7 |
| Lookalike Domains | DOM | 4 |
| Ransomware | RAN | 2 |
| Source Code Exposure | SRC | 5 |
| System Exposure | EXP | 6 |
| Total | 29 |
Identifier Format
All CTEM identifiers follow a consistent naming convention:
CTEM-[CATEGORY]-[NUMBER]
- CTEM: Continuous Threat Exposure Management prefix
- CATEGORY: Three-letter category code (e.g., INF, DOM, EXP)
- NUMBER: Sequential identifier within the category
This standardized format enables consistent communication, tracking, and integration across security tools and processes.