CTEM Stage 3: Prioritization
Stage Summary: Prioritization turns discovery data into an ordered plan. The objective is not to fix everything—it is to address the exposures most likely to be exploited and most damaging to the business.
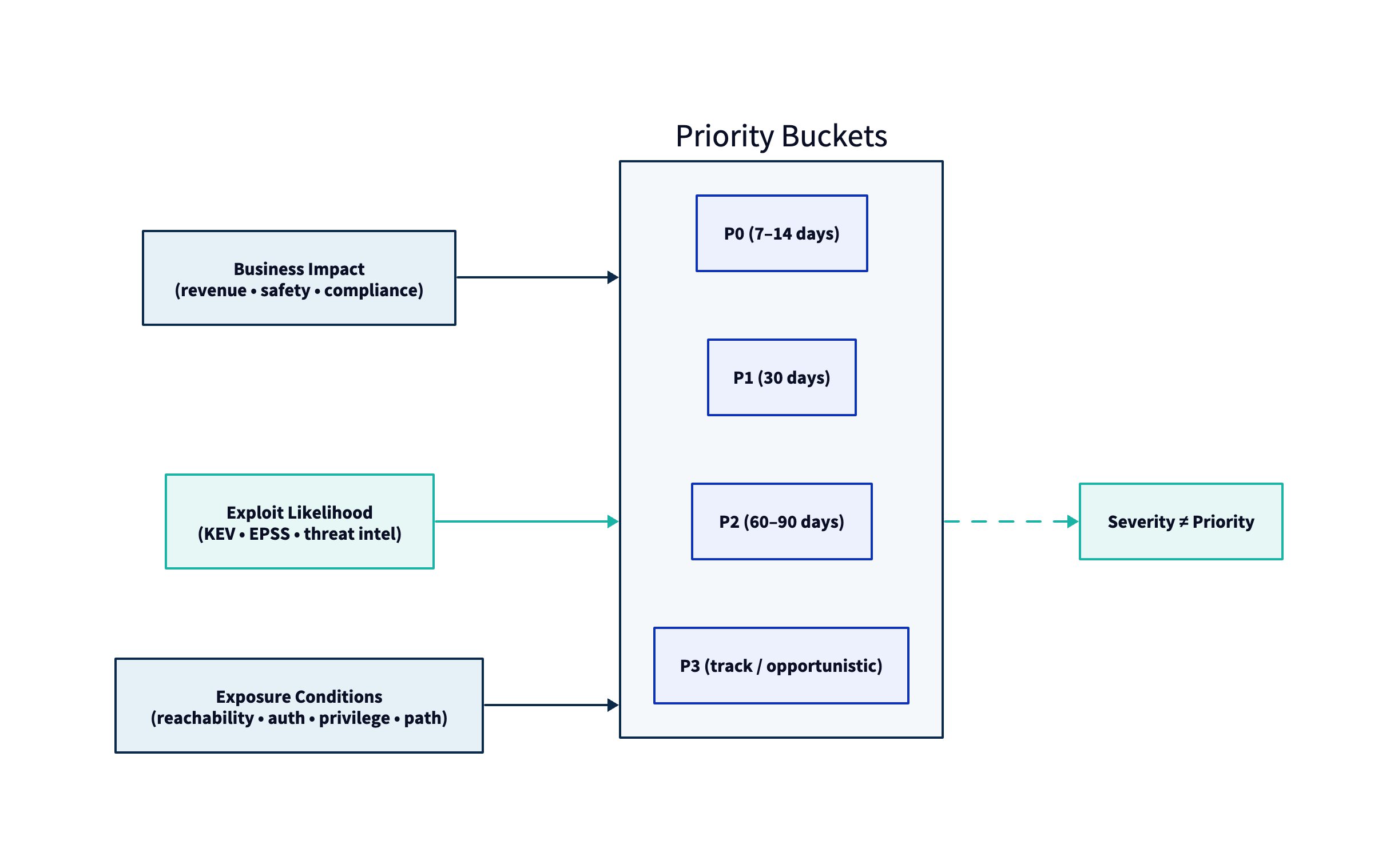
Why Prioritization Matters
Most enterprises cannot remediate every vulnerability or exposure they can measure—nor should they try. Prioritization is the control that prevents CTEM from degenerating into an unbounded backlog.
In Gartner’s CTEM framing, prioritization explicitly considers urgency, compensating controls, tolerance for residual attack surface, and risk to high-value assets. In other words, prioritization is a decision model, not a sorting function.
What Prioritization Produces
| Output | Purpose | Consumed by |
|---|---|---|
| Prioritized exposure backlog | A ranked remediation plan tied to business risk | Mobilization |
| Priority classes + SLAs | Predictable execution expectations | Engineering + ITSM |
| Exception/acceptance workflow | Governance of residual risk | GRC + leadership |
| “Why this is P0” rationale | Defensibility and stakeholder alignment | Everyone |
Key Activities
1. Combine Signals into a Transparent Model
A practical prioritization model blends four categories of signal:
- Business criticality of the affected asset/service
- Exploit likelihood
- Exposure conditions (reachability + prerequisites)
- Compensating controls and detection capability
Recommended external/public signals (non-vendor)
- CVSS: captures severity characteristics (not probability).
- EPSS: estimates probability of exploitation activity over a defined time horizon.
- CISA KEV: indicates vulnerabilities known to be exploited in the wild.
These are inputs—not answers. The model should remain explainable and auditable.
For many organizations, “In KEV + reachable + critical asset” is a reasonable P0 override, regardless of raw CVSS.
2. Define Priority Buckets and Default SLAs
One of the highest-leverage decisions you can make is to define priority classes that the business will actually honor.
Example priority policy (starter)
| Priority | Definition (example) | Default SLA |
|---|---|---|
| P0 | Known exploited (KEV) or validated exploit path to crown-jewel asset, reachable from assumed attacker | 7–14 days |
| P1 | High likelihood (high EPSS), reachable, high-impact service, limited compensating controls | 30 days |
| P2 | Medium likelihood or medium impact, compensating controls present | 60–90 days |
| P3 | Low likelihood and/or low impact, or not reachable in threat model | Track; fix opportunistically |
If your production change window is monthly, then a 7-day SLA implies compensating controls or emergency change processes—not optimism.
3. Incorporate Reachability and Preconditions
Two exposures with identical severity can represent radically different risk depending on exposure conditions:
- Internet-facing vs segmented
- Unauthenticated vs authenticated
- Requires admin privileges vs low privileges
- Attack-path adjacency (is there a plausible path from initial access to the asset?)
Treat these as first-class signals. If your discovery output cannot represent these conditions, improve discovery rather than compensating with guesswork.
4. Account for Compensating Controls (Without Hand-Waving)
Compensating controls are real—but only if you can defend them.
Examples:
- Segmentation that demonstrably blocks reachability from relevant sources
- Strong identity controls (phishing-resistant MFA) for sensitive admin planes
- Runtime protections (application allowlisting, hardened configs)
- Detection with proven coverage and response playbooks
If a compensating control is asserted, record:
- Which control is it?
- How is it validated?
- What failure mode would invalidate the assumption?
A Scoring Rubric You Can Operationalize
Avoid overfitting. The most common failure mode is a complex score no one trusts.
Example “weighted” model (illustrative)
- Impact score (0–5): based on business service criticality + CIA impact
- Likelihood score (0–5): EPSS percentile, KEV status, exploit maturity
- Exposure conditions (0–5): reachability + auth/prerequisites
- Control reduction factor (0–0.5): based on validated compensating controls
PriorityScore = (Impact + Likelihood + ExposureConditions) × (1 - ControlReductionFactor)