CTEM Stage 5: Mobilization
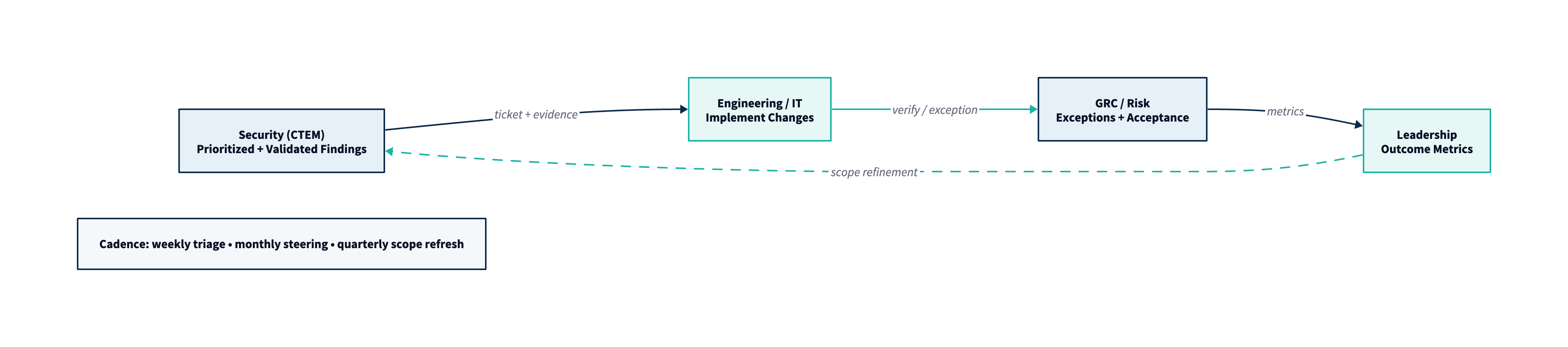
Stage Summary: Mobilization is where CTEM becomes real. It ensures that prioritized, validated exposures translate into executed remediation and measurable risk reduction—through clear ownership, workable processes, and outcome-based reporting.
Why Mobilization Matters
Most security programs do not fail because they cannot find exposures. They fail because they cannot reliably convert exposure insight into sustained operational change.
Gartner’s framing is explicit: mobilization is about people and process—reducing obstacles to approvals, implementation, and mitigation deployment. This is also where CTEM becomes legible to executives: you can show not just what is wrong, but what changed and what risk was removed.
Mobilization Outcomes
| Outcome | What it looks like |
|---|---|
| Work is routed to the right owners | Every P0/P1 has a named accountable team |
| Remediation is executable | Tickets contain evidence, risk context, and “definition of done” |
| Exceptions are governed | Acceptance is time-bound, approved, and re-validated |
| Metrics show risk reduction | Trend lines reflect validated exposure reduction, not discovery volume |
| The loop improves | Lessons feed back into scoping, discovery quality, and prioritization policy |
Key Activities
1. Convert Findings Into Actionable Work (Engineering-Grade)
A mobilization-grade work item answers, at minimum:
- What is the exposure and where is it? (asset identifiers)
- Why does it matter? (business service + impact)
- How do we know? (evidence from discovery/validation)
- What fixes are acceptable? (preferred fix + alternatives)
- How will we verify? (validation method and success criteria)
- When is it due? (priority/SLA and constraints)
Remediation ticket template (copy/paste)
Title: [P1] Reduce external exposure on <Service/Asset>
Business context:
- Service: <Business service name>
- Impact if exploited: <short statement in business terms>
Exposure summary:
- Exposure ID(s): <IDs>
- Asset(s): <domains/resources>
- Preconditions: <reachability/auth/prereqs>
Evidence:
- <link to sanitized evidence>
- First seen / last seen: <timestamps>
Remediation guidance:
- Preferred fix: <what “good” looks like>
- Alternatives/mitigations: <compensating control options>
Verification:
- Verification method: <re-test steps / control check>
- Definition of done: <observable conditions>
Owner / SLA:
- Assigned team: <team>
- Due date: <date>