The Five Stages of CTEM
Continuous Threat Exposure Management is not a product you buy—it is an operating model for systematically reducing the exposures that matter most to your organization. Gartner's CTEM framework breaks this work into five stages that form a continuous, iterative cycle.
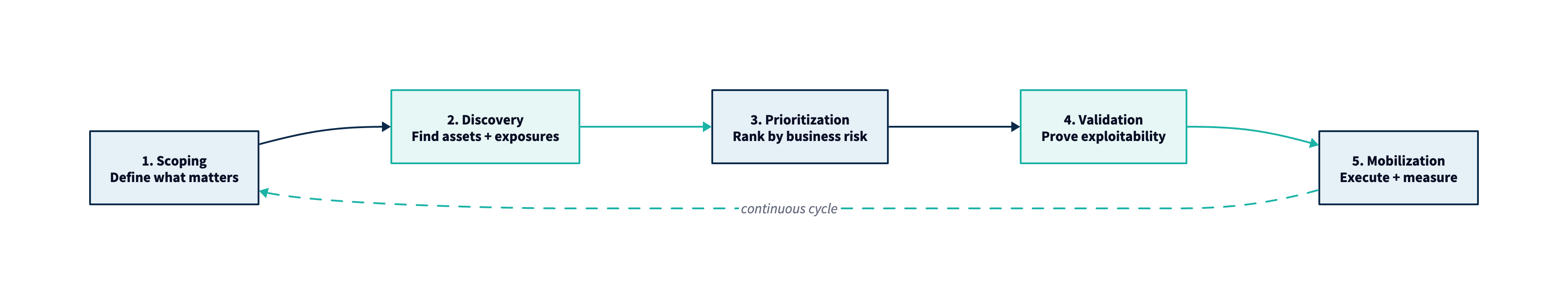
Each stage produces specific outputs that feed the next. When done well, the cycle tightens over time: scoping becomes more precise, discovery more accurate, prioritization more defensible, validation more efficient, and mobilization more predictable.
Stage Overview
1. Scoping
Purpose: Define what your CTEM program will protect and how you'll measure success.
Scoping prevents CTEM from becoming "vulnerability management for everything." You identify critical business services, map them to crown-jewel assets, define your attack surface boundary, and establish success metrics. A good scope is a business risk hypothesis—not a CMDB export.
What you'll find in this guide:
- How to identify critical assets from business impact backward
- Attack surface boundary templates
- Example scope charters and success metrics
2. Discovery
Purpose: Build continuous visibility into assets and exposures within your defined scope.
Discovery answers "what exists?" and "what's wrong with it?" across your boundary. This goes beyond CVE scanning—you're tracking misconfigurations, identity weaknesses, SaaS posture gaps, and third-party integration risks. The output is an evidence-backed exposure register, not just a findings list.
What you'll find in this guide:
- Asset inventory design principles (stable IDs, ownership, freshness)
- Exposure types beyond CVEs
- Data quality scorecards and normalization patterns
3. Prioritization
Purpose: Decide which exposures to address first based on business risk, not just severity.
Prioritization is a decision model that combines exploit likelihood (EPSS, KEV), business impact, exposure conditions (reachability, prerequisites), and compensating controls. The output is a defensible priority ranking with SLAs that engineering can actually meet.
What you'll find in this guide:
- Prioritization model combining CVSS, EPSS, and KEV
- Priority bucket definitions with realistic SLAs
- Scoring rubrics you can operationalize
4. Validation
Purpose: Confirm that priority exposures are actually exploitable and that controls work as expected.
Validation turns "theoretically risky" into "practically exploitable." You're testing whether attacks actually work in your environment, whether controls prevent/detect/respond as assumed, and whether fixes actually removed the exposure. This is continuous and scoped—not annual pen testing.
What you'll find in this guide:
- Rules of engagement and safety constraints
- Validation methods from config checks to adversary emulation
- Remediation verification checklists
5. Mobilization
Purpose: Convert validated findings into executed remediation and measurable risk reduction.
Mobilization is where CTEM becomes real. Findings become engineering-grade work items with evidence, owners, and SLAs. Exceptions are governed. Metrics show actual exposure reduction—not discovery volume. And lessons feed back into scoping for the next cycle.
What you'll find in this guide:
- Remediation ticket templates
- Cross-functional workflow patterns
- Outcome metrics that matter to leadership
How the Stages Connect
CTEM is explicitly continuous. Each cycle refines the next:
- Scoping gets sharper as you learn which assets and services actually drive risk.
- Discovery improves as you close ownership gaps and reduce staleness.
- Prioritization becomes more accurate as validation data reveals what's actually exploitable.
- Validation becomes more efficient as you build reusable test cases.
- Mobilization becomes more predictable as teams internalize the workflow.
The goal is not to run through the stages once—it's to run faster and more precisely over time, measurably reducing the exposures that matter most to your business.
Getting Started
If you're new to CTEM, start with Scoping. A focused first cycle (external attack surface or SaaS posture) will teach you more than trying to boil the ocean.
If you already have exposure data but struggle to act on it, jump to Prioritization or Mobilization to improve your decision model and remediation workflows.