CTEM vs Exposure Management
Exposure management is the broad discipline and outcome: reducing material cyber risk by shrinking exploitable conditions. CTEM is Gartner's structured, five-stage operating model for running exposure management continuously.
Figure 1: CTEM is best understood as a repeatable program structure for exposure management—not a replacement term for the discipline itself.
Overview
Security teams have always managed "exposures" in some form—patching critical vulnerabilities, hardening configurations, closing risky firewall rules, tightening identity controls, and responding to threat intel. What's changed is scale and rate of change: cloud, SaaS, CI/CD, third-party services, and identity sprawl create an environment where point-in-time assessments drift out of date quickly.
That's where modern exposure management thinking comes in: treat exposure reduction as a continuous, cross-domain risk program rather than a collection of siloed scanning and remediation activities.
CTEM is Gartner's attempt to make that operational: a five-stage cycle designed to help leaders continuously align assessment and remediation work to what is most material to the business (not merely what is most numerous in a scanner output). Gartner's public guidance lays out the stages explicitly—Scope, Discover, Prioritize, Validate, Mobilize—and emphasizes that the goal is not to fix everything, but to focus relentlessly on what most threatens the enterprise.
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes" and Gartner press release — Top Cybersecurity Trends for 2024 (Trend: CTEM).
At a glance: how the terms relate
| Dimension | Exposure Management (discipline) | CTEM (operating model) |
|---|---|---|
| What it is | The overarching practice of reducing an organization's risk exposure by finding and fixing exploitable conditions across the environment | A specific, named framework (Gartner) for executing exposure management as a continuous program |
| Core question | "What could realistically hurt us, and what do we do first?" | "How do we run this as a repeatable lifecycle with governance, validation, and follow-through?" |
| Scope | Can be narrow (e.g., internet-facing assets) or enterprise-wide (identity, cloud, endpoints, apps, SaaS, third parties) | Starts narrow by design (pilot scope) and expands iteratively through cycles |
| Output | Risk-informed remediation decisions, control improvements, and measurable reduction of exploitable attack paths | A structured set of artifacts and routines: scoped initiatives, prioritized backlogs, validation evidence, and mobilized remediation workflows |
| Failure mode | Becomes "vulnerability management with a broader dashboard," still disconnected from business impact | Becomes a "CTEM theater" label slapped onto tools without scoping, validation, or operational mobilization |
Terminology Clarification
"Exposure" is broader than "vulnerability"
In security conversations, "exposure" is often used casually to mean "a vulnerability we should patch." That framing is too narrow and routinely leads to noisy backlogs and misallocated remediation effort.
A more precise definition is closer to risk management:
- A vulnerability is a weakness that can be exploited or triggered by a threat source. (NIST definition)
- A threat is an event or condition that can cause loss/impact. (NIST definition)
- Exposure describes the extent to which an organization is subject to risk—often discussed in terms of likelihood and impact. (NIST definition)
In practice, an exposure usually exists when a weakness is present and reachable in a meaningful way, given the environment, control coverage, and plausible attacker behavior.
A useful mental model:
Exposure ≈ Weakness × Reachability × Exploitability × Business impact
(This isn't math; it's a reminder that severity alone is insufficient.)
That distinction matters because many of the exposures that drive real incidents are not "just CVEs":
- Misconfigurations (cloud/IaC, identity, network segmentation, SaaS settings)
- Excessive privileges and brittle trust relationships (identity and access paths)
- Internet-facing "unknown unknowns" (shadow IT, orphaned subdomains, forgotten services)
- Weak control efficacy (controls exist on paper but fail under adversary behavior)
Exposure management: a discipline, not a product category
You will see "Exposure Management" used as:
- a strategy ("we run exposure management across our environment"), and
- a market label for tools that correlate assets + weaknesses + threat intel + remediation workflows.
For CTEM.org, it's cleaner (and more accurate) to treat exposure management as the discipline and CTEM as a reference operating model that brings structure, cadence, and governance.
CTEM: Gartner's five-stage lifecycle
Gartner describes CTEM as a pragmatic, systemic approach to continually evaluate the accessibility, exposure, and exploitability of assets, and to align assessment and remediation to threat vectors or business initiatives rather than isolated infrastructure components.
See: Gartner press release — Top Cybersecurity Trends for 2024 (CTEM) and Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
If you're writing internal strategy docs:
- Use "exposure management" when you mean the end-to-end practice (identify → prioritize → validate → reduce exposure).
- Use "CTEM" when you specifically mean the five-stage Gartner lifecycle and its associated operating routines.
The CTEM Framework
CTEM is most useful when you treat it as program architecture—a way to reliably turn large volumes of security telemetry into a small number of high-confidence actions that reduce the probability of material loss.
The five stages (as described publicly by Gartner) are:
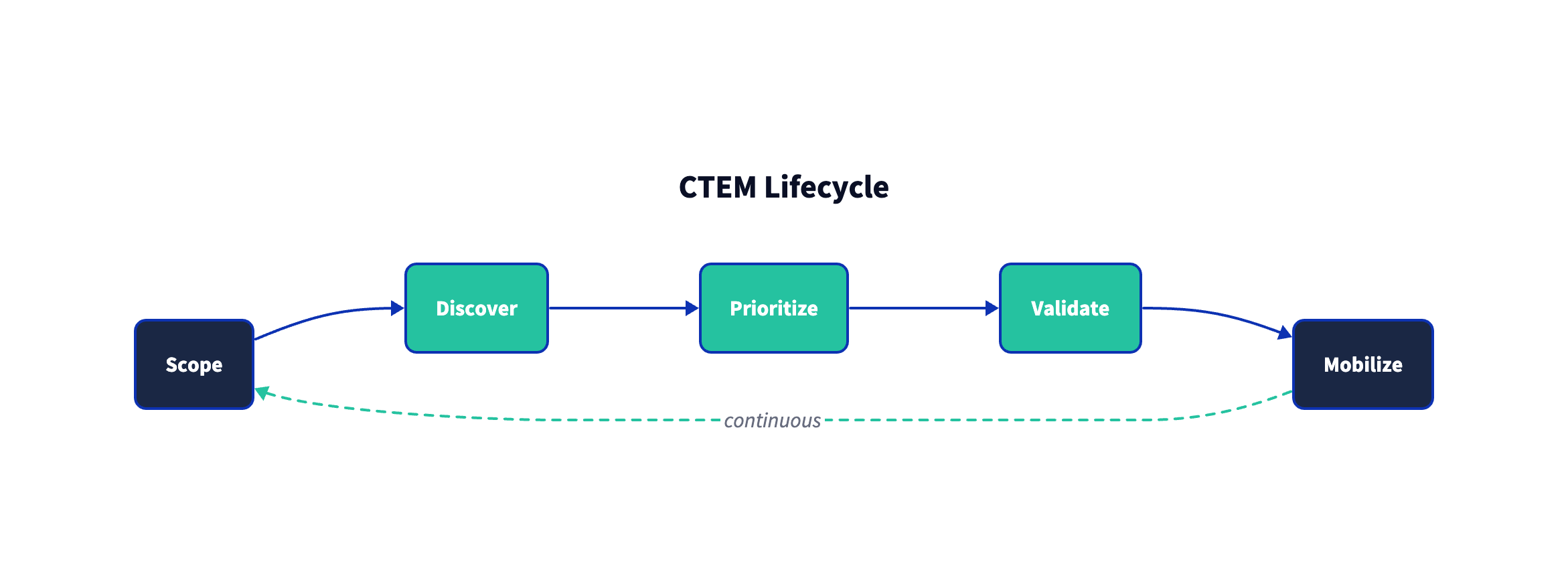
Figure 2: CTEM is a lifecycle. The value comes from repetition, tightening feedback loops, and continuously re-scoping toward what matters most.
Stage 1 — Scope: decide what "matters" before you measure
The highest-leverage step is also the one teams most often rush.
Scoping answers: "Which slice of the enterprise are we improving now, and why?"
Gartner explicitly recommends starting with a manageable pilot scope (e.g., external attack surface or SaaS posture) rather than attempting enterprise-wide coverage on day one.
See the scoping guidance in Gartner's public CTEM article: How to Manage Cybersecurity Threats, Not Episodes.
Good scoping is business-specific, and typically encodes:
- Material processes and assets (revenue paths, regulated data, critical production services)
- Threat-relevant vectors (internet exposure, identity, third-party access, cloud control plane)
- A success definition (risk reduction metric, control improvement, time-to-remediate for "must-fix" classes)
Anti-pattern: "We scoped everything."
If the scope is everything, it's not scope—it's avoidance of prioritization.
Stage 2 — Discover: build an evidence-based view of assets and exposures
Discovery is the collection and normalization step: assets, identities, control coverage, exposure signals, and the context required to interpret them.
In Gartner's framing, discovery should include "visible and hidden assets, vulnerabilities, misconfiguration and other risks," and it warns that teams often confuse scoping and discovery, mistaking volume for success.
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
Practitioner reality check: discovery is less about "finding more" and more about reducing uncertainty:
- Do we know what exists?
- Do we know how it's reachable?
- Do we know where compensating controls do (and do not) apply?
Stage 3 — Prioritize: decide what you will not do (yet)
Prioritization is where exposure management becomes materially different from legacy vulnerability management.
Gartner's public guidance emphasizes that the goal is not to fix every issue and lists prioritization factors such as urgency, availability of compensating controls, tolerance for residual attack surface, and risk posed to the organization.
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
A robust prioritization approach typically blends:
- Exploit evidence / exploit probability
- CISA's Known Exploited Vulnerabilities (KEV) Catalog is a practical signal for "exploited in the wild."
- FIRST's EPSS provides a probability estimate of exploitation activity over a short horizon.
- Reachability and attack-path plausibility (is it actually accessible from realistic attacker positions?)
- Business criticality and blast radius (what happens if this path is exploited?)
- Control reality (what controls exist, and do they meaningfully reduce likelihood/impact?)
Severity scores are useful, but they are not risk on their own. NIST's NVD explicitly states that CVSS supplies a qualitative measure of severity and is not a measure of risk:
NVD — CVSS Metrics
Stage 4 — Validate: prove what's exploitable and how defenses behave
Validation answers two questions that scanning alone cannot:
- Can an attacker actually do this in your environment?
- If they try, do your controls detect and contain it fast enough?
Gartner's public CTEM guidance frames validation as confirming exploitability, analyzing attack pathways, and assessing whether response plans are sufficient—plus aligning stakeholders on what triggers remediation.
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
Validation can be accomplished through multiple methods (the point is evidence, not any single technique):
- Adversary emulation (mapped to MITRE ATT&CK)
- Breach and attack simulation / purple teaming
- Targeted penetration testing tied to the current scoped initiative
- Control tests that confirm detection + response, not just prevention
Stage 5 — Mobilize: turn findings into action across teams
Mobilization is where CTEM is explicitly different from "continuous scanning." It's the operational mechanism that ensures prioritized and validated findings become real change:
- ticketing and ownership,
- approvals,
- implementation and rollout,
- exception handling,
- and measurement of completion and effectiveness.
Gartner's CTEM article is blunt here: you can't rely entirely on automated remediation; mobilization requires communicating the plan, aligning stakeholders, and documenting cross-team approval workflows.
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
Continuous vs Point-in-Time
A useful litmus test:
- Point-in-time assessment: "This is what we saw when we looked."
- Continuous exposure management / CTEM: "This is what matters now, and here is the closed-loop mechanism that will still matter next week."
CTEM is explicitly positioned as continuous, not episodic—moving away from annual pen tests and quarterly vulnerability reviews as the primary drivers of remediation priorities. Gartner's CTEM guidance frames this as managing "threats, not episodes."
See: Gartner — "How to Manage Cybersecurity Threats, Not Episodes".
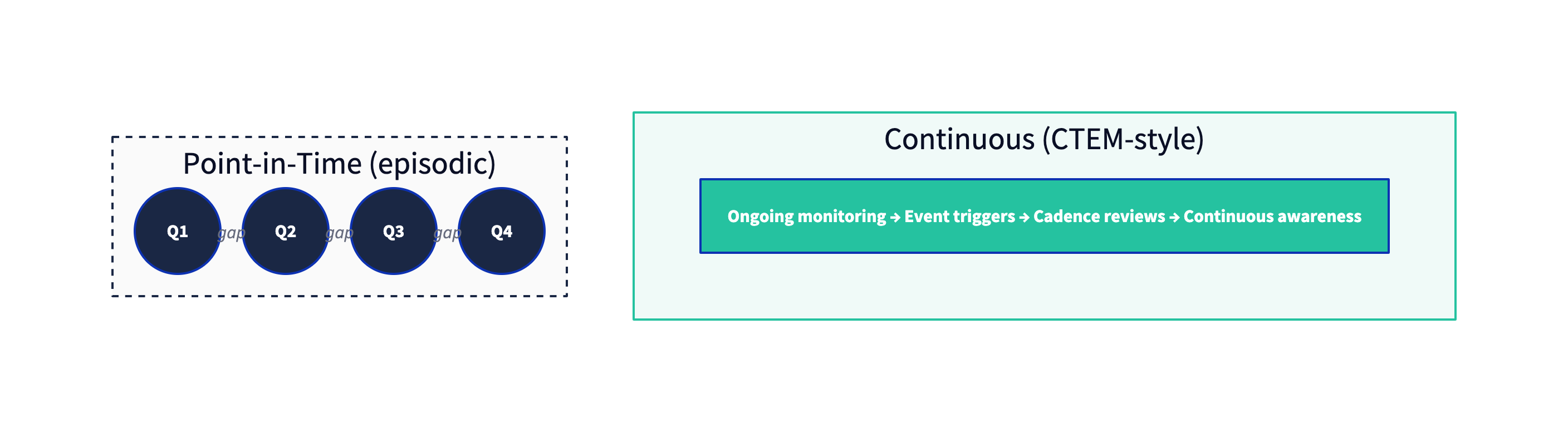
Figure 3: "Continuous" does not mean "scan every second." It means the program's priorities and actions are refreshed on a cadence that matches operational change and adversary tempo.
What "continuous" should mean operationally
A CTEM program is continuous when it has:
- A repeatable cadence (weekly/biweekly/monthly) for scoping updates, prioritization refresh, and stakeholder review
- Event-driven triggers (e.g., new internet-facing service, major SaaS onboarding, high-confidence exploit signals, KEV additions)
- A validation loop (prove exploitability and control behavior, don't assume it)
- A mobilization mechanism (ownership, SLAs, and exception paths)
Common failure modes to avoid
-
Discovery without scoping
Large inventories and dashboards are not "progress" unless they are tied to a scoped risk question and a remediation decision process. -
Prioritization that is still just severity sorting
Severity is not risk. Incorporate exploit evidence/probability and reachability/impact. -
Validation as an annual ceremony
Validation is most useful when it is narrowly targeted to the current scoped initiative and feeds back into prioritization. -
No mobilization pathway
Exposure reduction is a cross-functional outcome. If your engineering and IT partners experience CTEM outputs as "just another report," the program will stall.
Conclusion
If you're deciding which term to use:
- Use "Exposure Management" to describe the discipline: reducing risk by identifying, prioritizing, validating, and remediating exposures across the environment.
- Use "CTEM" to describe a specific, repeatable operating model for doing exposure management continuously: Scope → Discover → Prioritize → Validate → Mobilize.
For CISOs, the critical move is to shift the conversation from "How many vulnerabilities do we have?" to:
- Which exposures create credible attacker paths to material business impact?
- Which small set of fixes measurably reduces that risk this cycle?
- What evidence do we have that the fix is effective—and stays effective?
If you want one practical north star statement that is both accurate and actionable:
Exposure management is the goal. CTEM is a proven structure for running that goal as an ongoing program.
References & further reading (vendor-neutral)
- Gartner: How to Manage Cybersecurity Threats, Not Episodes
- Gartner: Top Cybersecurity Trends for 2024 (includes CTEM)
- NIST CSRC Glossary: Exposure, Vulnerability, Threat
- CISA: Known Exploited Vulnerabilities (KEV) Catalog
- FIRST: Exploit Prediction Scoring System (EPSS)
- MITRE: ATT&CK®
- NIST NVD: CVSS Metrics (severity, not risk)