CTEM vs EASM/CAASM
EASM and CAASM are tool categories. CTEM is an operating model (a program framework). In practice, EASM/CAASM most directly support the Discovery stage of CTEM, but CTEM only works when Discovery is connected to business scoping, risk-based prioritization, real-world validation, and cross-functional mobilization.
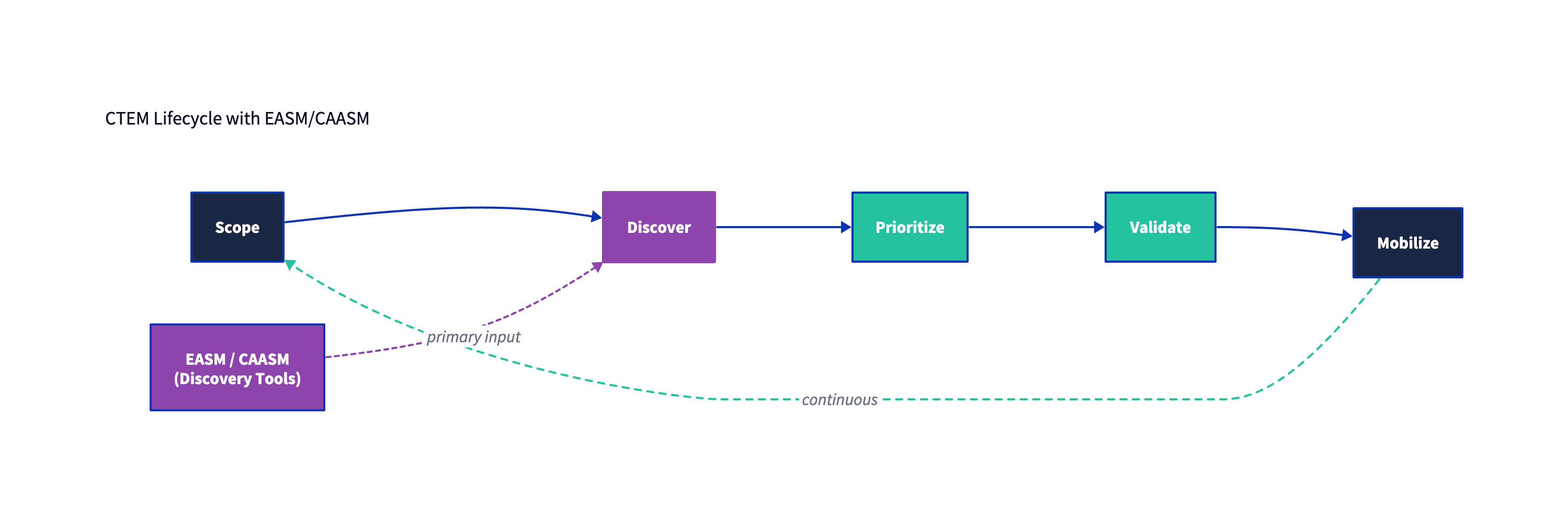
Figure 1: CTEM is a continuous cycle; EASM/CAASM primarily contribute to Discovery, and also provide key inputs to Prioritization and Mobilization.
Overview
Most security teams already collect huge volumes of asset and exposure data. The hard part is turning that data into a repeatable, business-aligned reduction in material risk.
Gartner describes CTEM as a five-step process: scope, discovery, prioritization, validation, and mobilization — oriented toward surfacing and actively prioritizing what most threatens the business, not just producing more findings.
For organizations piloting CTEM, Gartner explicitly calls out the external attack surface as a pragmatic starting point due to its narrower scope and ecosystem maturity, and also highlights SaaS posture as another common initial focus area.
See: Gartner: How to Manage Cybersecurity Threats, Not Episodes
A quick framing that avoids common failure modes
- CTEM is how you run the program. It is a lifecycle that repeatedly narrows and refines attention onto what matters most.
- EASM helps you see what the internet sees. It discovers and monitors internet-facing assets and exposures — including those you may not realize you own.
- CAASM helps you reconcile what you think you own with what your tools observe. It unifies asset and exposure data across internal and external environments, primarily by integrating with existing sources of truth and security tools.
If EASM/CAASM answer “what exists and what looks exposed?”, CTEM answers “what matters, what is exploitable, what do we do next, and who is accountable?”.
CTEM vs EASM vs CAASM at a glance
| Dimension | CTEM (program framework) | EASM (tool category) | CAASM (tool category) |
|---|---|---|---|
| What it is | An operating model for continuously reducing threat exposure | Technology + process to discover and monitor internet-facing assets/exposures | Technology to unify visibility of assets/exposures across environments, often via integrations |
| Primary lens | Business outcomes and attacker-relevant exposure | Outside‑in (“what an attacker can see”) | Inside‑out / federated (“what our systems say exists”) |
| Typical data sources | Whatever is relevant to the scoped initiative (EASM, CAASM, VM, CSPM, IAM, appsec, etc.) | DNS, certificates, web/port scanning, cloud footprints, attribution signals | CMDB, cloud inventories, EDR, vuln scanners, IAM, ticketing, SaaS admin, network tools, etc. |
| Core outputs | A prioritized, validated backlog + mobilized remediation plan | External inventory + exposures + change detection | Consolidated asset graph + exposure/control gaps + ownership/context |
| Main risk | Program devolves into “just another dashboard” | Noise, misattribution, and unverifiable findings if not validated | Garbage-in/garbage-out if integrations are incomplete or stale |
What is EASM?
External Attack Surface Management (EASM) focuses on discovering and monitoring the internet-facing assets and exposures that could be exploited by threat actors — including assets that are unknown, unmanaged, or incorrectly attributed inside the organization.
Gartner defines EASM as processes, technology, and services used to discover internet-facing enterprise assets and systems and exposures that could be exploited, and emphasizes its value in identifying unknown assets and understanding what is visible in the public domain.
Reference: Gartner Peer Insights: External Attack Surface Management (definition section)
What EASM typically covers well
EASM implementations vary, but strong programs/tools commonly support:
- Asset discovery and attribution
- Domains, subdomains, certificates, IP space, cloud-hosted workloads, external apps/APIs
- Subsidiaries and business units (where attribution is often messy)
- Exposure discovery
- Weak or expired TLS configurations, exposed admin services, misconfigurations
- Publicly reachable services that are out of policy (shadow IT and “orphaned” systems)
- Continuous change detection
- “What changed since last week?” is often more actionable than a static list
- Evidence for triage
- Screenshots, banners, headers, response bodies, certificate chains, and other artifacts that make findings easier to verify
What EASM is not (and why that matters)
- Not a replacement for authenticated vulnerability scanning. External discovery is largely unauthenticated; it’s excellent for reachability and posture signals, but not a full substitute for internal telemetry.
- Not automatically “your problem.” A core challenge is attribution (e.g., shared hosting, MSP-managed assets, inherited DNS, acquisitions, and third-party services).
- Not “done” at inventory. Success is measured by risk reduction and remediation outcomes, not by discovering more assets.
If the EASM output can’t be tied to an owner and an SLA-backed remediation process, it becomes a perpetual list of “interesting things we found on the internet.”
What is CAASM?
Cyber Asset Attack Surface Management (CAASM) focuses on giving security teams a consolidated, queryable view of assets and exposures across the enterprise — spanning on-prem, cloud, and SaaS — and identifying gaps in visibility and security controls.
Gartner describes CAASM as enabling organizations to see all assets (internal and external) primarily through API integrations with existing tools, querying consolidated data, and identifying vulnerabilities and gaps in security controls — then monitoring and analyzing those vulnerabilities to prioritize remediation.
Reference: Gartner Peer Insights: Cyber Asset Attack Surface Management (definition section)
What CAASM typically covers well
- Asset graph construction / identity resolution
- Normalizing “the same asset” across multiple data sources (EDR, cloud inventory, vuln scanners, CMDB, IAM, etc.)
- Control coverage and blind spot detection
- “Which critical assets are missing EDR?”
- “Which internet-facing assets are not in CMDB?”
- “Which cloud accounts are not monitored by CSPM?”
- Exposure consolidation
- Surfacing the intersection of: vulnerable + exposed + business-critical + lacking compensating controls
- Ownership & routing context
- Mapping assets to teams, apps, or business services — which becomes foundational to mobilization
What CAASM is not (and why that matters)
- Not an authoritative source of truth by itself. CAASM is often best viewed as a reconciliation layer that exposes inconsistencies between existing systems.
- Not magic asset discovery. If a device/workload/app never appears in any integrated source, CAASM won’t conjure it into existence.
- Not a substitute for governance. Without agreed naming, ownership, and lifecycle practices, CAASM will faithfully aggregate disagreement.
EASM vs CAASM: the practical differences CISOs should care about
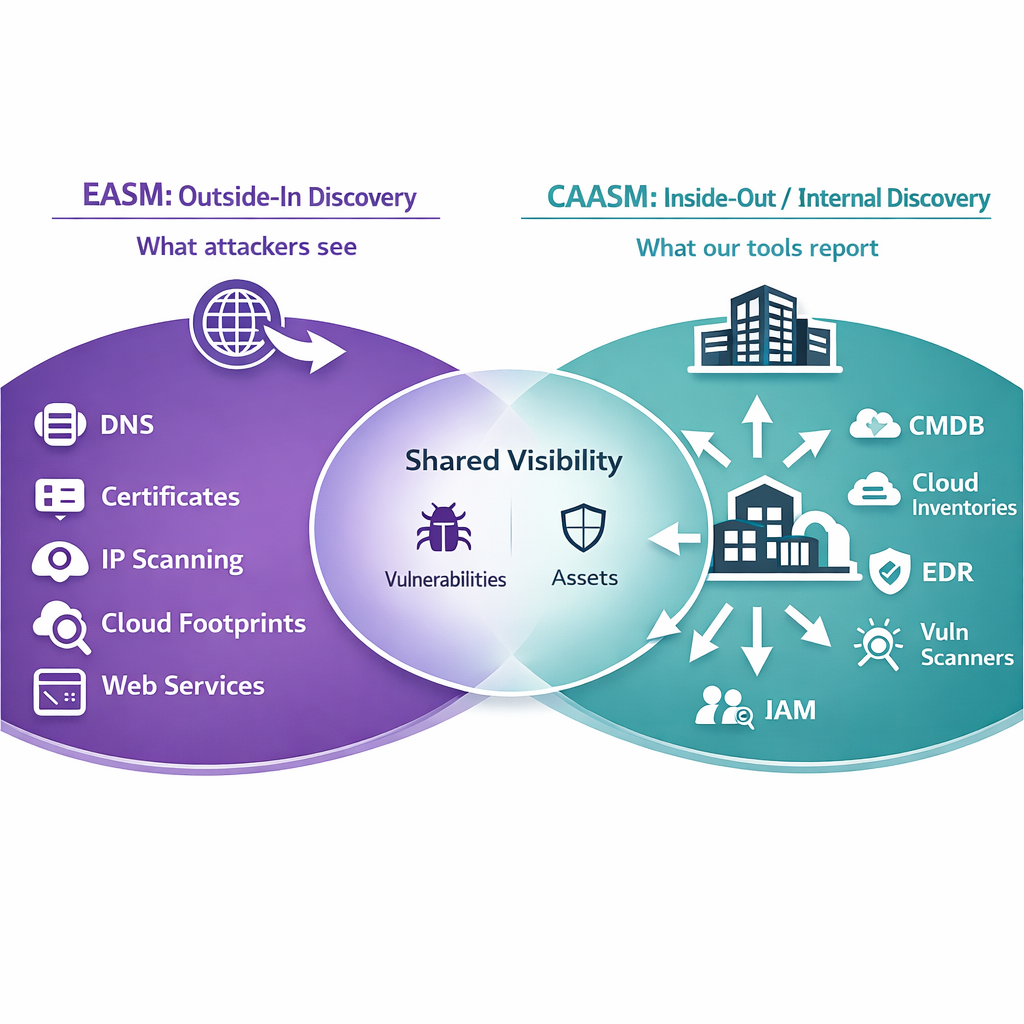
Figure 2: EASM is predominantly outside‑in; CAASM is predominantly inside‑out/federated. Mature programs use both — and accept that neither is perfect alone.
A useful mental model is: EASM finds what you didn’t know was exposed; CAASM explains why it happened and who can fix it.
| Question | EASM tends to answer better | CAASM tends to answer better |
|---|---|---|
| “What does an attacker see from the internet?” | ✅ | ⚠️ (only if integrated with EASM/edge telemetry) |
| “What assets do we have across cloud/on‑prem/SaaS?” | ⚠️ (external subset) | ✅ |
| “Which critical assets lack required controls?” | ⚠️ | ✅ |
| “Who owns this exposed thing?” | ⚠️ (hard) | ✅ (if ownership sources exist) |
| “Is this exploitable in our environment?” | ⚠️ (needs validation) | ⚠️ (needs validation) |
Where EASM/CAASM Fit in CTEM
Gartner’s CTEM process is explicit about two points that matter operationally:
- Discovery is not the same as scoping. Confusing the two is a common early failure: discovering more assets is not success if the scope is wrong.
- Discovery must capture more than CVEs: it should include hidden assets, vulnerabilities, misconfiguration, and other risks relevant to the scoped initiative.
Reference: Gartner CTEM five-step process
CTEM stage mapping
| CTEM Stage | What “good” looks like | How EASM/CAASM contribute |
|---|---|---|
| Scoping | Define the slice of the business you are protecting (processes, crown jewels, threat scenarios) | Provide initial asset boundary hypotheses (domains, cloud accounts, SaaS tenants) and reveal “unknown unknowns” that refine the scope |
| Discovery | Enumerate assets and exposures within the scoped boundary | Primary contribution: EASM discovers external footprint and exposures; CAASM consolidates enterprise asset/exposure data and reveals coverage gaps |
| Prioritization | Rank what to fix based on exploitability, business impact, and compensating controls | Provide key inputs: reachability, ownership, control coverage, vulnerability/exposure context |
| Validation | Confirm exploitability and plausible attack paths; test whether controls respond | Provide targets, context, and evidence that improve validation efficiency and reduce false positives |
| Mobilization | Remove organizational friction; drive remediation with clear accountability and workflow | CAASM is often strongest here (ownership mapping, routing, SLAs); EASM helps track external regression and re-exposure |
Beyond Discovery: what CTEM does that EASM/CAASM do not
EASM and CAASM can dramatically improve your visibility, but visibility alone does not reduce exposure. CTEM forces the program to confront three hard questions:
- Which exposures matter to our business and threat model?
- Which of those exposures are realistically exploitable (and by what path)?
- Can we reliably mobilize remediation across the teams that own the risk?
1) Scoping: business-first, not tool-first
Gartner’s CTEM guidance frames scoping as defining your “attack surface” (vulnerable entry points and assets) beyond typical vulnerability management, including less tangible elements like social media accounts, code repositories, and integrated supply chain systems.
Reference: Gartner CTEM scoping guidance
A pragmatic scoping approach that scales:
- Start with 1–2 exposure “slices” where you can measure impact:
- External attack surface for a critical business service
- A specific SaaS estate (e.g., identity provider + critical SaaS apps)
- A high-value cloud landing zone
- Define exit criteria that are observable (e.g., “all internet-facing admin portals require MFA and are behind approved access paths”)
- Decide up front how you will treat third‑party managed exposure (contractual levers, compensating controls, or acceptance)
2) Prioritization: stop treating “severity” as “risk”
A mature CTEM program uses multiple inputs — because no single score is a risk oracle.
Two practical, defensible inputs security teams increasingly combine:
- CVSS: communicates technical severity of vulnerabilities (and supports environmental tailoring in v4.0)
Reference: FIRST CVSS v4.0 specification and NVD announcement on CVSS v4.0 support - EPSS: estimates probability of exploitation activity in the wild over the next 30 days; importantly, EPSS is not a risk score and should be treated as one signal among many
Reference: FIRST EPSS User Guide and FIRST EPSS Model
In other words:
- CVSS ≈ impact/severity characteristics
- EPSS ≈ exploitation likelihood signal
- Your environment ≈ reachability, control posture, and business impact
Also, where you have access to exploited-vulnerability intelligence, it’s rational to treat that as a strong prioritization signal. The U.S. National Vulnerability Database (NVD) notes that CVE pages identify vulnerabilities appearing in CISA’s Known Exploited Vulnerabilities (KEV) catalog and emphasizes the value of prioritizing remediation of those vulnerabilities; U.S. federal agencies are required to remediate KEV-listed vulnerabilities within prescribed time frames under Binding Operational Directive (BOD) 22‑01.
Reference: NVD notice on KEV mapping
3) Validation: prove exploitability and attack paths
Gartner’s CTEM process explicitly calls out validation as:
- confirming attackers can actually exploit a vulnerability,
- analyzing attack pathways to the asset,
- and ensuring response plans are fast and substantial enough.
Reference: Gartner CTEM validation guidance
Why this matters in EASM/CAASM-heavy programs:
External and consolidated asset data creates hypotheses. Validation turns hypotheses into actionable truth and reduces wasted cycles.
Practical validation methods include:
- Adversary emulation / purple teaming for scoped attack paths
- Continuous control validation against relevant TTPs
- Targeted penetration testing driven by CTEM prioritization outputs
- Attack path analysis and segmentation testing (where relevant)
4) Mobilization: the part most “tools-first” programs miss
Gartner is blunt that mobilization cannot rely solely on “automated remediation”; it requires communicating the plan to security and business stakeholders and removing obstacles in approvals and implementation workflows.
Reference: Gartner CTEM mobilization guidance
Mobilization is where CTEM becomes a management system rather than a telemetry project.
High-leverage mobilization patterns:
- Make ownership mandatory: every externally reachable asset has an owner/team and a contact path
- Treat “unknown owner” as a P1 data quality defect (not a shrug)
- Integrate remediation into the systems teams already live in (ITSM, Jira, engineering backlogs)
- Define “definition of done” beyond patching (e.g., control coverage restored, exposure regression tests in place, monitoring confirmed)
How to operationalize EASM/CAASM inside a CTEM program
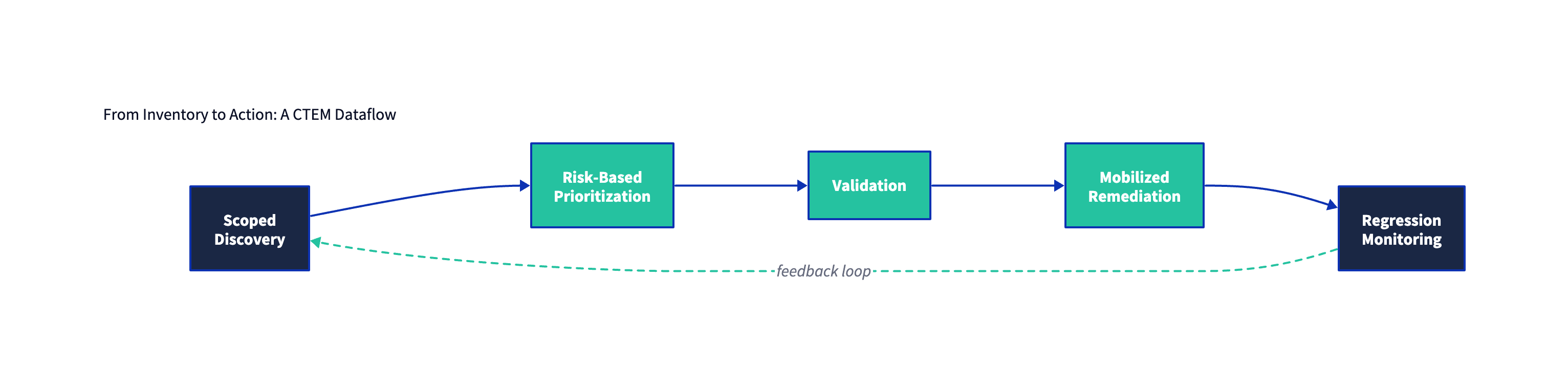
Figure 3: The winning pattern is a closed loop: scoped discovery → risk-based prioritization → validation → mobilized remediation → continuous regression monitoring.
A pragmatic integration blueprint
-
Normalize assets
- Assign a stable asset identifier strategy (domain, cloud resource ID, device ID, SaaS tenant object IDs)
- Deduplicate aggressively (this is where many CTEM attempts stall)
-
Attach business context
- Criticality, business service mapping, data sensitivity, user exposure, regulatory relevance
-
Enrich with likelihood signals
- Exploit intelligence, reachability, exposed attack paths, and (where applicable) EPSS-style probability signals
-
Validate the top slice
- Validate the highest risk items, not the longest list
-
Mobilize with measurable SLAs
- Explicit cross-team agreements: routing, exceptions, acceptance criteria, regression monitoring
Metrics that reflect exposure reduction (not tool output)
Avoid vanity metrics like “number of assets discovered.” Prefer metrics that indicate reduced attacker opportunity:
- Time to identify new internet-facing assets (MTTD for new exposure)
- Time to assign ownership for new assets/exposures
- Time to remediate top-priority exposures (MTTR by severity and exploitability)
- Coverage gaps on critical assets (e.g., % lacking EDR / MFA / logging)
- Regression rate (how often remediated exposures reappear)
Selection considerations (vendor-neutral)
You can evaluate EASM/CAASM capabilities without turning the exercise into a feature checklist. Anchor your evaluation to CTEM outcomes:
EASM evaluation questions
- Attribution confidence: What evidence supports “this belongs to us”?
- Change detection: How clearly can it show what changed and when?
- Evidence quality: Can findings be verified quickly without heroics?
- Asset modeling: Does it model apps/APIs and cloud-hosted assets well, not just IPs?
- Workflow: Can it route findings to owners with context and acceptance criteria?
CAASM evaluation questions
- Integration breadth and depth: Which sources are first-class and how often do they update?
- Identity resolution: How does it reconcile duplicates and conflicting truths?
- Control coverage analytics: Can it answer “what’s missing” reliably?
- Queryability: Can engineers and analysts ask ad-hoc questions without custom ETL?
- Export and interoperability: Can you get normalized data out for CTEM prioritization and reporting?
Conclusion
- CTEM is the program: scope → discover → prioritize → validate → mobilize — repeatedly, with measurement and accountability.
- EASM is a discovery lens: it shows the organization’s internet-facing reality, including unknown and unmanaged assets.
- CAASM is a reconciliation layer: it consolidates and normalizes what your enterprise tooling already knows (and reveals what it doesn’t).
The most mature security organizations do not treat EASM or CAASM as “the CTEM platform.” They treat them as inputs into a disciplined exposure management loop — one that produces fewer surprises, faster validation, and remediation that sticks.